Forewarned is forearmed, and the case of FluBot malware is no exception, as it is poised to spread further.
FluBot malware, which was first seen in Spain in late December 2020 by ESET, has spread to Germany, Poland, Italy and the Netherlands, among other countries, in 2021. Notorious for delivering text messages (SMS) with links to download malicious apps, FluBot has chiefly targeted Android, but also iPhone, users.
While FluBot has gone through several development stages, in the penultimate version 3.9, FluBot began campaigning in Italy and using Cloudflare’s DNS over HTTPS service, an encrypted protocol that resolves domain names to IP addresses. Now, in version 4.0, FluBot is continuing to expand its horizons with code suggesting it’s gearing up to strike a larger batch of countries around the world for the first time – or, in some cases, yet again – including the UK, Denmark, Finland, Sweden, Norway and Japan.
Android users who protect their mobile devices with ESET Mobile Security are also protected from FluBot and can find any detections of the malware named as a variant of the Android/TrojanDropper.Agent family. However, as many Android users may not be protected with a mobile security solution, and are thus more vulnerable to falling to this threat, let’s take a closer look at the ruses employed by FluBot, and offer some advice to stay safe.
An “innocent” SMS from your parcel delivery service?
FluBot’s operators typically launch their campaigns by sending SMS messages en masse, with one of various messages related to shipping and delivery accompanied by a malicious link. In March 2021, ESET telemetry picked up an SMS targeting Android users in Germany with the message: “Your package is arriving, track it here.”
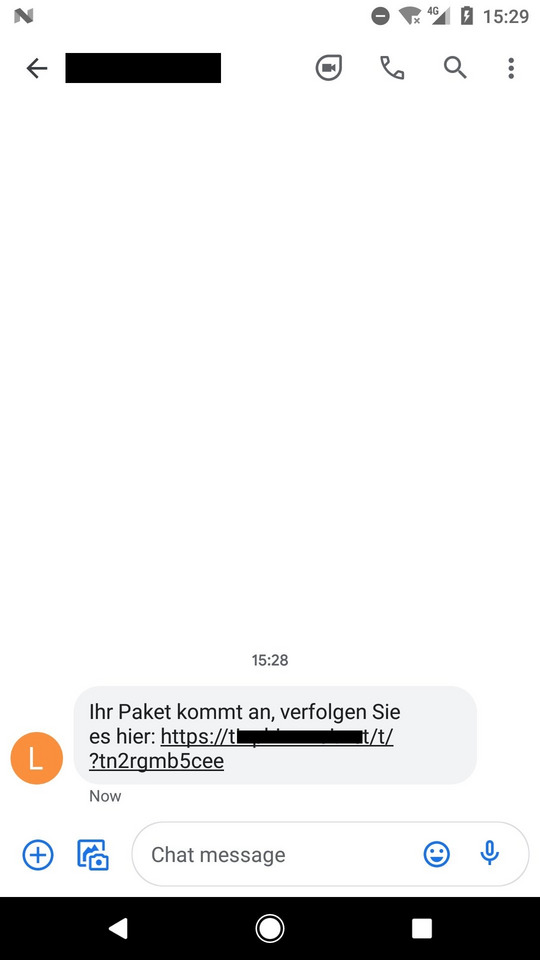
This particular campaign in Germany started on March 15 and victimized dozens of users within a few days. Other examples of messages include:
- UPS: Your package is arriving. UPS online tracking: gdtmtx[.]com/4/
- Hello {username}. Please confirm your delivery details today, or your package will be returned: witheaseappareloptin[.]com/app/
- Hello, your shipment was delivered on 05/03-2021 to the shipping depot. See where you can pick up your package here: ekremakin[.]org/pack/
- NACEX ADVISES: THE STATUS OF PACKAGE 303/03445873 ABSENT WITH NOTICE. YOU CAN MANAGE FROM visotka[.]in/pack/ OR TLF.936372200
- We weren’t able to deliver your package. Click on the link to create a new delivery date: sekolahalmunasemarang[.]sch[.]id/url/
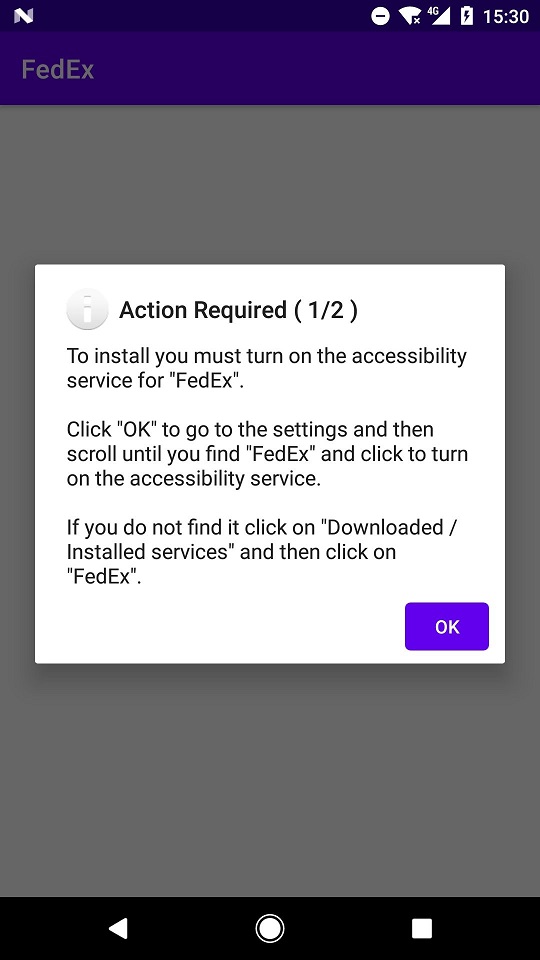
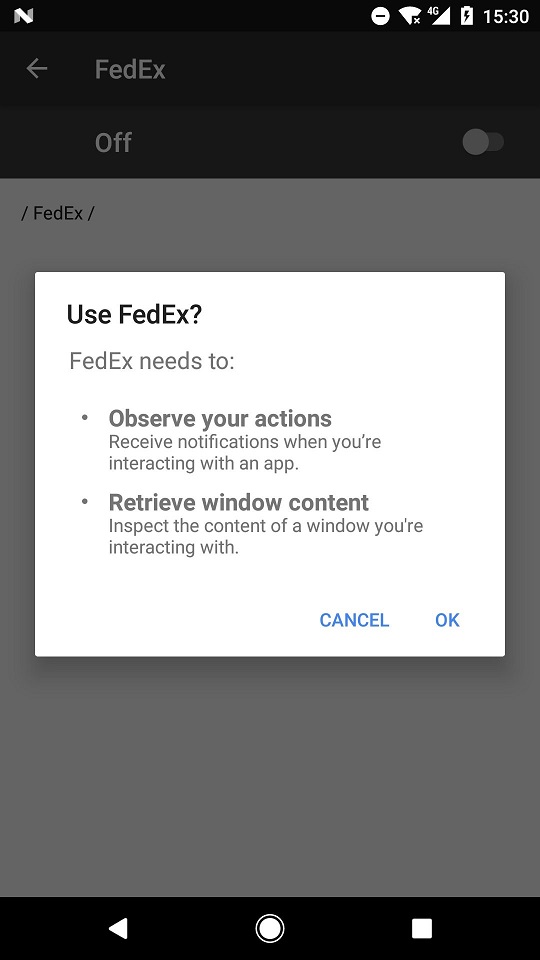
Anyone duped into clicking on the malicious link is sent to a webpage posing as an international logistics company like DHL, FedEx, or, most recently, UPS. Of course, regional and local logistics companies are also within the scope of FluBot’s impersonations. The purpose of this ploy is to get Android users to download and install a malicious app laced with FluBot, like the FedEx app in the images below:
Note that the real FedEx Mobile app does not ask for permission to use accessibility services.
Once installed, the malicious app is able to detect other apps on the mobile device related to banking or cryptocurrencies. The next time users open one of these financial apps, FluBot can then superimpose a convincing, but fake, overlay window over the original application to steal their credentials.
iPhone users are also not exempt from being targeted by FluBot – the difference being there is no malicious app on offer. Instead, a phishing scam is used, such as a fake Amazon survey that requests credit card details with the false promise of a reward.

Exploring the scale of FluBot’s campaigns
In the first two months of FluBot’s campaigns – from the end of December 2020 to the end of February 2021 – the main target was clearly Spanish Android users. At the end of February, one estimate found that as many as 60,000 Android devices in Spain had fallen victim to FluBot. In addition, over 11 million phone numbers, nearly all belonging to Spanish residents, had been harvested by FluBot’s operators.
Shortly thereafter, in early March, several news reports claimed that part of the criminal gang behind FluBot had been detained in a police operation in Barcelona. However, that information was wrong, as the gang arrested were using websites, not malicious apps, to impersonate logistics companies such as Correos (the Spanish national mail service) and steal credit card info. Moreover, considering that the FluBot attacks continued after those unrelated arrests and that the malware is advertised in underground hacking forums, FluBot’s developers are clearly still at large and selling their wares as malware-as-a-service.
Indeed, with the success of FluBot attacks in Europe, other malicious actors have been copying FluBot’s tactics of using SMS messages and malicious apps impersonating logistics companies. For example, that’s the case with TeaBot (aka Anatsa and Toddler), another Android banking trojan discovered in January that switched from using fake media players to fake apps impersonating logistics companies.
Be wary of malicious SMS messages, fake apps and other tricks
Seeing the rapid expansion of FluBot campaigns in the past few weeks, keep in mind the following advice:
- Think twice before clicking on a link sent via SMS. Instead, go to the official website and type in any purported tracking numbers to verify they are genuine.
- Do not download apps from outside official app stores like Google Play.
- Be wary of the permissions you grant to applications. If you notice that the requested permissions are suspiciously inappropriate for the app’s stated purpose, that may be a red flag that you are dealing with a malicious app.
- Before downloading an app, do some research on the developer, and the app’s ratings and user reviews. Pay special attention to negative reviews – some apps are simply too good to be true.
- Use a reputable security solution like ESET Mobile Security.
- If you have fallen into the misfortune of installing a malicious app, you can follow the steps from ESET researcher Lukaš Štefanko’s video detailing how to identify a malicious app and boot your phone in safe mode to uninstall it.