What does XDR mean for ESET and how does its pursuit give perspective on MITRE Engenuity’s ATT&CK® Evaluations?
One of the main goals of MITRE Engenuity’s ATT&CK® Evaluations is to help organisations better understand the level of visibility that endpoint detection and response (EDR) solutions offer when investigating real time, sophisticated threats lurking in a network. Visibility is a crucial metric in any organisation’s assessment of an EDR solution it is considering to implement.
ESET’S 2022 ATT&CK EVALUATION RESULTS
Obviously, visibility is not the only metric. The additional metrics considered in the ATT&CK Evaluations largely centre around the context that accompanies the detection of specific adversarial techniques. These have a varying level of importance to each organisation, depending on its level of maturity, the different regulations it needs to comply with, and a host of other sector-, company-, and site-specific needs. Yet there are other metrics, such as performance and resource requirements, alert fatigue, integration with other security software, and ease of use, that aren’t always considered in evaluations.
This rich palette of metrics in part reflects the success of EDR as a go-to tool for security defenders. Even organisations without dedicated security teams are interested in this type of defence tool. Yet the market is pushing EDR to become even more advanced. Often, security defenders juggle between an EDR solution to hunt down threats and a security information and event management (SIEM) solution to sifting through big data sets as complementary activities to defend their networks — the strategy being that what is lacking in one tool can be made up for by the other.
Some might think that if only a synthesis could be achieved between EDR and a security analytics platform security defenders would have the ultimate tool in their hands. However, Forrester analysts see the situation differently. EDR needs to evolve into extended detection and response (XDR) by learning to ingest data feeds sourced beyond endpoints for analysis and response. Budding XDR solutions can then enter into a toe-to-toe competition with security analytics platforms in a race that appears destined for collision.
On the other side, to remain competitive, security analytics platforms need to be equipped with EDR features like higher-quality alerts and threat response capabilities and use resources more efficiently. The evolved solution that demonstrates better overall security is likely to become the increasingly favoured tool for defenders. Our bet is that XDR has the winning odds because of its stronger foundation on EDR solutions that are designed for higher-quality detections with rich context, even if partially limited in overall visibility.
What does XDR mean for ESET?
ESET adopts Forrester’s understanding of XDR as the next generation of EDR that moves beyond endpoints to collect data also from network devices, email servers, cloud-based services, and other sources and allows security defenders to discover and respond to more threats. In order to achieve this increased level of data collection and response capability, XDR can use two integration strategies: hybrid and native.
A hybrid strategy focuses on integrations with third-party tools. A native strategy focuses on integrations with tools from the same vendor. Currently, no vendor offers a complete XDR solution, making it an ideal yet to be achieved.
ESET is committed to building out a full XDR solution by iteratively improving ESET Inspect (formerly ESET Enterprise Inspector) and continuing to add integrations both with ESET’s ecosystem of security tools and with third-party tools. Previously, as ESET Enterprise Inspector, ESET’s EDR solution was positioned for enterprise security teams. Now, as ESET Inspect, it has evolved into the XDR-enabling component of the ESET PROTECT platform, ready for both large enterprise and smaller security teams.
Before looking at the ESET PROTECT platform, let’s consider ESET Inspect a little more closely.
ESET Inspect: Enabling the pursuit of XDR
More than being a mere name change, ESET Inspect is a new version with increased visibility and remediation capabilities. ESET Inspect carries over the familiar features of previous versions, such as the referencing to the MITRE ATT&CK knowledge base in its rule set, a REST API for integration with security orchestration, automation, and response (SOAR), SIEM, ticketing and other similar tools, and the ability to run a remote PowerShell session on Windows machines for precise response and remediation options.
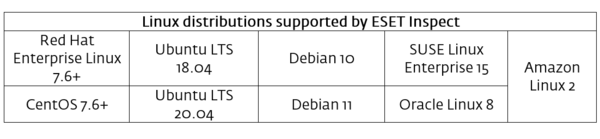
In the latest version of the product — version 1.7 — several major Linux distributions are now supported. This adds to the already existing support for Windows and macOS and marks an important milestone on the road to a complete XDR solution. ESET Inspect’s coverage for Linux machines works in concert with ESET Endpoint Antivirus for Linux and ESET Server Security for Linux (from versions 9.0) to support the following distributions:
ESET Inspect also features an expanded rule set currently consisting of almost 1,000 rules. The rules are used to analyse events happening on endpoints, firewall and network data, user account actions, and other data for potentially malicious behaviours to be investigated by security engineers.
ESET researchers have enhanced a selection of rules with automated responses, for instance, to isolate a computer or block an executable. The use of an automated response in specific rules is made visible in the “Active Rule Actions” column of the “Detection rules” view:
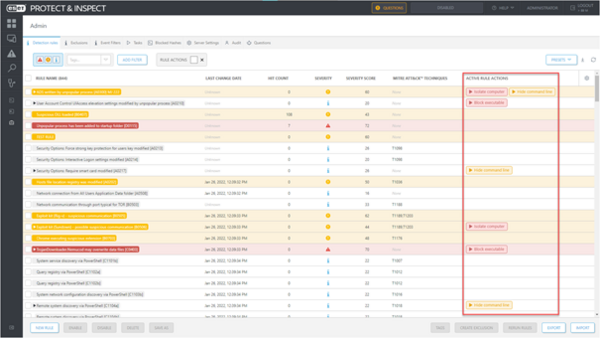
Figure 1. ESET Inspect’s rules can trigger automated responses
The continued growth of ESET Inspect’s rule set and its integration with ESET’s other security products is a good example of building a native XDR solution. For ESET, the core of this integration lies in ESET PROTECT, a management console for IT admins to deploy and configure ESET security products. The ESET PROTECT platform packages endpoint security, server security, encryption, cloud-based, and detection and response solutions with the console to provide businesses a scalable prevention, detection, and response capability.
Thus, positioning ESET Inspect more closely to ESET PROTECT helps create a more integrated experience for security defenders using ESET’s security ecosystem. As mentioned above, one of the key goals of an XDR solution is to incorporate threat data beyond just endpoints, meaning that continuing to extend ESET Inspect’s coverage to more platforms and data sources that are already integrated with ESET PROTECT puts it firmly on the road to that goal.
Lifting ESET PROTECT Enterprise toward XDR
ESET is building an XDR solution on the ESET PROTECT Enterprise platform, which packages ESET Inspect along with endpoint and server protection, cloud-based threat detection, and encryption to provide a comprehensive security capability.
XDR demands more data for ingestion, but this necessitates a need for greater database storage capacity that can hit performance hard if not adequately handled. Investing in more hardware to support on-premises database solutions is always possible, even if lacking some flexibility. This is why thinking ahead about the database needs for ESET PROTECT and the database needs for ESET Inspect is crucial.
With a cloud deployment, however, scaling up to meet this data storage demand is much more flexible as there is no need to buy new hardware. The cost lies rather in renting more storage space and possibly more powerful machines — a change that can be executed rapidly. The flexibility and scalability offered by the cloud are precisely the qualities required of an XDR solution, as Forrester points out.
Formerly, ESET PROTECT and ESET Inspect were only available for on-premises deployment, which could require considerable hardware investment, server maintenance costs, and on-site staff. While on-premises deployment remains an option, especially for organisations more keen to keep their data close to hand, both these solutions are also available in the cloud — a new capability for ESET Inspect since version 1.7 — and thus answer XDR’s call for cloud-native support.
Managed detection and response
In some cases, especially for smaller organisations or those whose core focus is outside of security, extracting value from an XDR solution can be too heavy of a lift to make unassisted. Similarly, managing ESET PROTECT Enterprise requires either full-time security staff or a managed detection and response (MDR) provider to take over some, if not all, of the daily security work.
For some time, the manufacturers and developers of complex products have recognised the need to increase the value of their products with a service offering. This is because at times customers struggled to see the value of their purchase when they did not have the expertise to use the product well, often misconfiguring it or failing to use all its features. More importantly, offering services reflects the type of relationship that providers wish to have with customers — for ESET that means engaging in a security partnership with customers.
ESET’s revamped MDR service assists security teams to set up ESET’s products with the best configuration and optimisations possible for their networks. The service also includes periodic health checks to address any poor security practices or misconfigurations that may have crept in over time. Critically, organisations can request the help of ESET security engineers for on-demand or proactive threat hunting with ESET Inspect.
Interested organisations (in select countries) can explore their options by reaching out via ESET’s MDR service web page.
Conclusion
This article started by discussing visibility and all the other metrics that organiations need to look at when considering a detection and response solution. For a snapshot of the depth of visibility that ESET Inspect can provide threat hunters, read the blogpost: Hunting down Sandworm and Wizard Spider: How ESET fared in the ATT&CK® Evaluations.
Designing a detection and response solution that balances all these metrics is by no means an easy task. The brief journey through XDR taken here has revealed a complexity of issues in developing native and hybrid integrations for EDR solutions and in scaling up data collection via cloud deployments, all while making detections of high quality and rich with context and maintaining high system performance.
While there are certainly mature organisations ready to wade through this complexity, the tough reality for most is that they may have only one or two IT administrators ... and they are managing security part time, along with their many other responsibilities. This can make the ATT&CK Evaluations, which concentrates on sophisticated threat groups, or even a discussion about XDR appear as somewhat of a niche focus.
However, both the evaluations and the pursuit of XDR speak to the scope of security practices — from basic configurations and policies all the way to advanced fine-tuning and optimisation — that should be in place to protect against even the most common threats. Furthermore, XDR’s demand for the cloud opens the door to improved security even for organisations without dedicated security teams. Such organisations may discover that their security practice falls short of industry standards when engaging in this discussion. At least in this way — by beginning the game of catch-up on their security — the ATT&CK Evaluations and the pursuit of XDR can provide actionable insight even to less mature organisations.