1bn+
users worldwide
400k+
business customers
ESET Mobile Device Management for Apple iOS
Set-up, configure and monitor all company iOS devices from a single pane of glass. Enables:

Anti-theft

Web content filtering

Applications white/black listing

Device security
Significant security increase
Left up to a user, device security is usually not implemented properly. ESET allows you to define password complexity requirements, set screen lock timers, prompt users to encrypt their device, block cameras and more.
Simple licensing
Mix and match your license seats exactly as you need. Migrate seats from one device to another, regardless of the OS.
Remote management
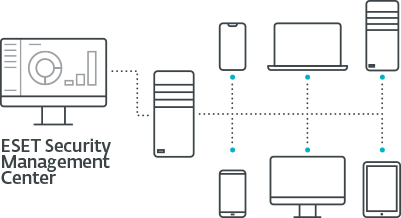
No need for dedicated solutions - ESET Mobile Device Management for Apple iOS comes integrated within ESET Security Management Center, giving you a single point of overview of network security, including all endpoints, mobiles & tablets and servers.
Use cases
PROBLEM
Organizations are not only concerned with devices being lost or stolen, but also with data theft when an employee is terminated.
SOLUTION
- Enforce security policy that requires mobile devices to be encrypted.
- Implement security policies that require passcodes or pins to be set on all devices.
- Lock-out or remotely wipe devices when needed.

protected by ESET since 2017
more than 9,000 endpoints

protected by ESET since 2016
more than 32,000 endpoints
The ESET difference
Anti-theft
Remotely lock/unlock devices or wipe all the data they hold in case they are lost or stolen.
App white/black listing
White/black list apps to prevent users from installing prohibited apps and manage app notifications to users.
Push account settings remotely
Remotely push out account settings such as Wi-Fi, VPN and Exchange information.
Web content filtering
Adult web content, as defined by Apple, can be blocked. The admin can also white/black-list specific URLs.
Explore our customized solutions
Please leave us your contact details so we can design a personalized offer to fit your requirements.
No commitment.
System Requirements
- Operating Systems:
iOS 8+ - ESET Remote Administrator Mobile Device Connector
- Company Apple iTunes ID Compatible with ESET Security Management Center and ESET Remote Administrator 6. See more information about remote management compatibility.
Looking for complete security for your network?
Related enterprise-grade solutions
ESET Endpoint Protection Advanced
- Security Management Center
- Endpoint Protection Platform
ESET Identity & Data Protection
- Two-factor Authentication
- Endpoint Encryption
Related products and services
- ESET Security Management Center
Real-time network security visibility, reporting and management on a single screen. - ESET Endpoint Security
Award-winning multilayered technology combining machine learning, big data and human expertise. - ESET Endpoint Security for Android
Light-footprint endpoint security including antimalware, anti-phishing and anti-theft. - ESET Secure Authentication
Powerful Two-factor authentication makes access to networks and data safe and problem-free.
Looking for the complete security of your network?
Related enterprise-grade solutions
ESET Endpoint Protection Advanced
- Security Management Center
- Endpoint Protection Platform
ESET Identity & Data Protection
- Two-factor Authentication
- Endpoint Encryption
Related products and services
- ESET Security Management Center
Real-time network security visibility, reporting and management on a single screen. - ESET Endpoint Security
Award-winning multilayered technology combining machine learning, big data and human expertise. - ESET Endpoint Security for Android
Light-footprint endpoint security including antimalware, anti-phishing and anti-theft. - ESET Secure Authentication
Powerful Two-factor authentication makes access to networks and data safe and problem-free.
Stay on top of cybersecurity news
Brought to you by awarded and recognized security researchers from ESET's 13 global R&D centers.