Get APT reports you can act on – quickly and accurately
Putting our best research at your fingertips
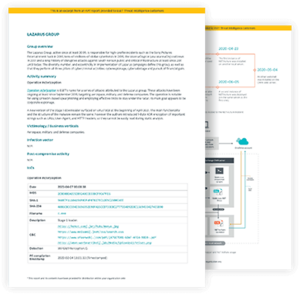
Our research team is well known in the digital security environment, thanks to our award-winning We Live Security blog. Their great research and APT activity summaries are available, with much more detailed information at your disposal.
Actionable, curated content
Reports provide a great deal of context to what is going on and why. Thanks to this, organisations can prepare in advance for what might be coming. It’s not just the reports themselves – they are curated by our experts who put them in a human-readable format.
Make crucial decisions fast
All this helps organisations to make crucial decisions and provides a strategic advantage in the fight against digital crime. It brings an understanding of what is happening on the ‘bad side of the internet’ and provides crucial context, so that your organisation can make internal preparations quickly.
Access to ESET Analyst
Every customer ordering the APT Reports PREMIUM package will have also access to an ESET analyst for up to four hours each month. This provides the opportunity to discuss topics in greater detail and help resolve any outstanding issues.
In-depth analysis
The package includes in-depth technical analysis reports describing recent campaigns, new toolsets and related subjects, and activity summary reports. A monthly overview combines information from all Technical Analysis and Activity Summary reports released in the previous month into a shorter and more digestible form.