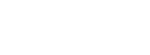ESET Threat Intelligence reports and feeds
Get in-depth, up-to-date global knowledge about specific threats and attack sources. Use the expertise of our IT team, because it can be difficult for security engineers, who access information only within their own networks, to detect these threats. Enable your organization to:
Detect Advanced Persistent Threats (APTs)
Block suspicious domains
Prevent botnet attacks
Block Indicators of Compromise
Improve resilience to attacks
In order to manage risks and effectively implement the Zero Trust framework, organizations need more than just information about what's happening on their own network. The latest information on the threat landscaped helps better prevent attacks, even before they strike. In order to face these threats, companies need to create robust systems that help protect, mitigate and investigate security problems, so that business continuity remains unaffected.
Act on comprehensive information
Threat Intelligence platforms can provide a lot of data and potentially overwhelm organizations with information. It's crucial that businesses are able to act quickly on information they receive, without the need for exhausting analysis. Speed is of the essence when taking the threat intelligence data out of a report and feed, and blacklisting the Indicators of compromise (IoCs) or alerting internal security staff. Feeds and reports must be highly contextual to ensure a quick response.
Get the big picture
It's important that threat intelligence data you receive is not only actionable, but also easily and comprehensively integrated in your environment. Support for out-of-the box integration into TI systems and third party SIEMs is a must; as is support for industry standard formats such as TAXII, so that integrating with in-house tools is also possible.

受ESET保护 自2017年以来
9,000多个端点

受ESET保护 自2016年以来
超过14,000个端点
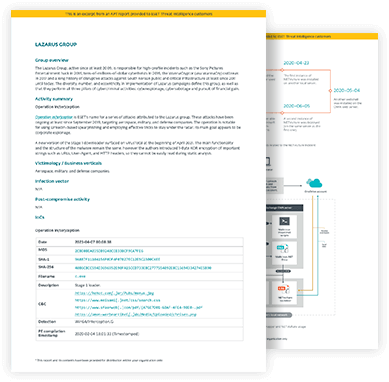
Get APT reports you can act on – quickly and accurately
Putting our best research at your fingertips
Our research team is well known in the digital security environment, thanks to our award winning We Live Security blog. Their great research and APT activity summaries are available, with much more detailed information at your disposal.
Actionable, curated content
Reports provide a great deal of context to what is going on and why. Thanks to this, organizations can prepare in advance for what might be coming. It’s not just the reports themselves – they are curated by our experts who put them in a human-readable format.
Make crucial decisions fast
All this helps organizations to make crucial decisions and provides a strategic advantage in the fight against digital crime. It brings an understanding of what is happening on the ‘bad side of the internet’ and provides crucial context, so that your organization can make internal preparations quickly.
ESET proprietary intelligence feeds
Get a quick, real-time look at the worldwide threat landscape. Our feeds come from our research centers based around the globe to get a holistic picture, and quickly block IoCs in your environment. Feeds are in the formats • JSON • STIX 2.0
Malicious files feed
Understand which malicious files are being seen in the wild. Features domains which are considered malicious, including domain name, IP address, detection of file downloaded from URL and detection of the file which was trying to access the URL. This feed is shared hashes of malicious executable files and associated data.
Domain feed
Block domains which are considered malicious including domain name, IP address, and the date associated with them. The feed ranks domains based on their severity, which lets you adjust your response accordingly, for example only block high-severity domains.
URL feed
Similar to Domain feed, the URL feed looks at specific addresses. It includes detailed information on data related to the URL, as well as information about the domains which host them. All the information is filtered to show only high confidence results and includes human-readable information on why the URL was flagged.
Botnet feed
Based on ESET's proprietary botnet tracker network, Botnet feed features three types of sub-feeds – botnet, C&C and targets. Data provided includes items such as detection, hash, last alive, files downloaded, IP addresses, protocols, targets and other information.
Explore our customized solutions
Please leave your contact details so we can design a personalized offer to fit your requirements.
Related business solutions
Service
Managed Detection & Response
The ultimate fusion of cutting-edge security tools and top of the line human expertise.
Security solution
ESET PROTECT Enterprise
Cyber risk management and visibility into IT environment, including Endpoint Detection and Response.
Protection category
Cloud sandbox
Cloud-based sandboxing technology that detects never before seen or zero-day threats.